About cookies on this site Our websites require some cookies to function properly (required). In addition, other cookies may be used with your consent to analyze site usage, improve the user experience and for advertising. For more information, please review your options. By visiting our website, you agree to our processing of information as described in IBM’sprivacy statement. To provide a smooth navigation, your cookie preferences will be shared across the IBM web domains listed here.
Financial Services
How to build a vault for your digital wallet
20 November, 2019 | Written by: Anna Shugol
Categorized: Financial Services
Share this post:
Custody – foundation of the digital assets market?
With the rise of platform banking infrastructure and armed with digital banking licenses, fintech startups are quickly bringing traditional and blockchain banking services. These services potentially upend the establishment with new forms of capital formation, liquidity, and efficiencies in payments and managing assets. Institutional investors, crypto hedge funds, exchanges, token issuance platforms, private banking, Wall Street titans, and others have started using digital assets for lending, depository, escrow and payments services.
This new financial infrastructure is built upon a foundation of institutional digital asset custody. The custody responsible for safe guarding private keys, settlement, compliance reporting, asset servicing, and corporate actions. Today’s digital asset custody service providers are going beyond purely offline digital asset storage to provide passive income to their clients while safekeeping their assets.
What do you think when you hear the word – “vault”? It immediately springs the picture of a metal door with levers hidden in the depths of a bank securing physical assets. Indeed, before bank accounts were federally insured, bank customers often considered their bank’s vault size and strength when shopping for places to keep their valuables such as gold, art, wills, and bearer instruments like bonds, stock certificates, and cash.
The bullet-proof door was keeping all those precious assets away from the thieves and the ones who were not supposed to obtain them. The biggest disadvantage of that approach was that amount of time needed to access the market – to either sell, trade, or manage non-liquid assets.
Now with that picture in mind, what do you think when you hear the word “digital vault”?
Digital vaults are different, instead of keeping a physical asset, these contain their digital analogues, a digital asset. Almost any asset can be represented in a digital way, unlocking the possibilities for trading, selling, and instant liquidity. Whether this is something tangible (a house, a car) or intangible (bond, shares, will – proof of ownership) – it can be represented as a digital token. If you want to learn more on programmable money, I recommend reading the IBM report.
Modern digital vaults use wallets to manage the existential risk of losing the digital assets with the practical need to make them available for monetization via lending, collateral, and staking. The degree to which these wallets make their assets available online is often referred to as hot (online), cold (offline), and warm (on-demand). Once the predominant style, cold wallets are yielding to warm wallets and this is where the digital asset custody market is headed.
According to Fidelity Investments, it is estimated that 22% of institutional investors already hold direct or indirect positions in new digital assets with 40% being open to future investments.
The expectations for securing a digital vault are significantly more and the impact of losing a digital key is far more critical. With the expansion of digital services portfolio, it is up for an every custodian to think about the implementation of a bank vault – but in a digital way.
The protection of a digital asset requires a trusted execution environment, with the following attributes:
- Authentication and authorization policies
- Bespoke transaction approval policy: multi-party, multi-quorum transaction signing
- HSM embedded transaction logic
- Resiliency and availability.
The asset is cryptographically secured with a pair of keys – public and private. The private key represents a key to the vault – and its loss or corruption leads to the catastrophe.
The hackers’ attacks have got sophisticated as well, introducing new techniques for obtaining the private key – which equals to obtaining the key to the vault. Different malicious attacks are targeting various levels of the environment, trying to find the weakest spot and use it for non-sanctioned access. The recent hacker attacks are showing the frightening trend: you don’t know who will attack. Today’s digital asset custody solution providers face existential threats from all sides – and the rise of internal attacks is shocking.
In these demanding circumstances, where stakes are very high – literally, business owners should focus on building a digital vault that meets the requirements for high performance throughput and security.
The current digital wallets security technologies are aimed to solve one particular problem at a time, however, leaving others at risk. It is equal to placing a giant lock on a vault’s door – but leaving the keys in a public space.
Only a comprehensive approach that addresses all potential security risks can satisfy the market’s high expectations in the area of custody.
Trusted digital platform should combine all latest and time-proven technologies to secure the digital wallets and stay compliant and auditable in the same time.
The platform should provide automated, pervasive encryption for the applications (wallets), databases and on-demand secure access to the digital assets.
Hardware-based cryptography should be preferred to the software one, as it has proved to be more effective and stable. Multi-level encryption with several keys is important to exclude different types of cyber-attacks.
All the wallets and sensitive clients’ data require trusted execution environment, encrypted by multiple keys (multi-level of encryption). All the data, both at-rest and in-flight, must be protected and encrypted to support all kinds of digital wallets.
Cryptographically locked down execution runtime, no code injections, no data extraction, no root access, no backdoors, no malware loading – this is how IBM is already addressing these requirements by having introduced Hyper Protect Digital Assets Platform. Platform is an essential and a fundamental component for bringing your digital assets services to your clients – in a highly trusted, secured, resilient and performant way.
Platform’s core components:
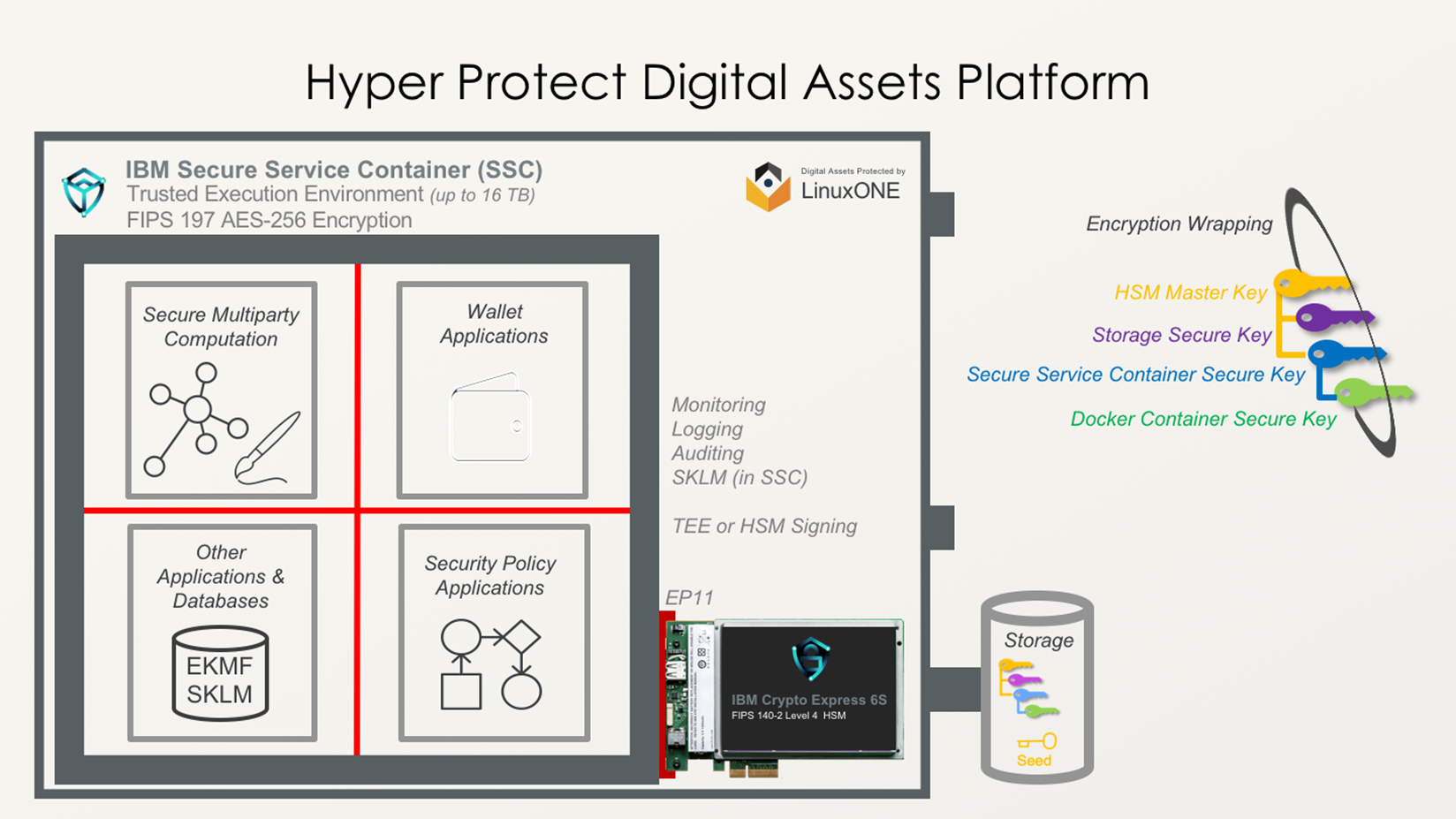
The platform contains all the attributes for building the trusted foundation for the custody of the assets. Start-up Digital Asset Custody Services (DACS) has recognized a gap in the market for a trusted environment for digital asset transactions. DACS engaged IBM to help it build a full-suite digital asset servicing platform for enterprise businesses, designed to scale alongside clients’ needs and efficiently integrate with other client environments. The full case study can be found here
IBM is uniquely positioned to help build a trusted digital asset foundation to deliver on demand warm wallet capability, that supports any digital asset type from coins to non-fungible assets like digital wills, while thwarting malicious actors inside and out. Programmable money, custody, digital assets and custody
If you’re interested in keeping up to date with the ever changing market, why join one of our IBM Open Breakfast Club meetups. The meetup schedule can be found here. I look forward to seeing you there and discussing the latest technologies and market trends.

Anna Shugol
IBM Z Client Technical Specialist
More Financial Services stories
By Col Chambers and Ed Gillett on 5 February, 2025
Preparing for the defence of the Realm
In light of current conflicts, the UK is now faced with real-world military decisions that will affect our immediate future. Ed Gillett and Col Chambers assert that industry and government must switch to a readiness mindset before the European post-war peace shatters. “My vision for the British Army is to field fifth-generation land […]
By Juan Bernabe Moreno and others on 12 December, 2024
Frontier Fusion: Accelerating the Path to Net Zero with Next Generation Innovation
Delivering the world’s first fusion powerplants has long been referred to as a grand challenge – requiring international collaboration across a broad range of technical disciplines at the forefront of science and engineering. To recreate a star here on Earth requires a complex piece of engineering called a “tokamak” essentially, a “magnetic bottle”. Our […]
By Nick Levy on 9 December, 2024
Safer Technology Change in the Financial Services Industry
Many thanks to Benita Kailey for their review feedback and contributions to this blog. Safe change is critical in keeping the trust of customers, protecting a bank’s brand, and maintaining compliance with regulatory requirements. The pace of change is never going to be this slow again. The pace of technology innovation, business […]





























