About cookies on this site Our websites require some cookies to function properly (required). In addition, other cookies may be used with your consent to analyze site usage, improve the user experience and for advertising. For more information, please review your options. By visiting our website, you agree to our processing of information as described in IBM’sprivacy statement. To provide a smooth navigation, your cookie preferences will be shared across the IBM web domains listed here.
Security
Securing cyber-physical systems with IBM-Exalens co-created CPDR solution
30 June, 2023 | Written by: M Shaikh, Julia Rodgers, and Ryan Heartfield
Categorized: Security
Share this post:
On December 23, 2015, in the heart of winter, several Ukrainian power companies were targeted by hackers in a well-planned cyberattack. Suddenly, almost a quarter-million people found themselves without electricity, and the companies affected were scrambling to restore power.
This wasn’t a random malware that happened to sneak in – the attack was specifically designed to target the companies’ Operational Technology (OT) systems. The attackers had studied the power grid’s Industrial Control Systems (ICS) inside and out and knew exactly how to cause the maximum amount of disruption.
Here’s the part that is humorously ironic in retrospect: the systems were so heavily automated and relied so much on the compromised OT systems that the companies had to literally dust off their old manual equipment to restore power.
Yes, you read it right. In the middle of one of the most sophisticated cyberattacks the world had seen until that point; Ukrainian power engineers were resorting to manual operations – workers physically turning wheels and flipping switches – to get the lights back on!
This devastating event underscored the importance of OT security. More than many others, this incident led to an increased global emphasis on OT security, a push for international cooperation in combating cyber threats, and the recognition that OT systems are as much a target as any IT system.
So, while it’s bizarre to picture modern engineers reverting to manual methods, the key takeaway is clear: robust OT security isn’t optional – it’s a necessity.
The Growing Problem of Cyber-Physical System Security
Approximately 30.7 billion operational technology (OT) devices are expected to be in use by 2023, according to Gartner. OT Security incidents have seen an increase of 250% in the past five years and the average cost of an OT security breach has reached $1.8 million. More attacks are now focused on cyber-physical systems compared to other operational technologies, with an increase in the number of attacks, the cost of a breach and the sophistication of attacks. This makes sense considering that CPS are often connected to IT systems, are more vulnerable and are applied in critical infrastructure, transportation, healthcare, etc.
Adversaries that target critical infrastructure have shown a deep understanding of control system components, industrial protocols, and engineering operations. This knowledge has allowed them to launch increasingly sophisticated and disruptive attacks, from the Maroochy Shire Sewage Spill in 2000 to the more recent Incontroller/PIPEDREAM attack framework. These attacks have the potential to cause physical damage and economic disruption, and industrial security defenders must address new challenges and threats to protect critical infrastructure.
Double-Edged Sword of IT-OT Convergence: Opportunities and Risks in the Age of Hyper-Connectivity.
IT and OT convergence is exacerbating the OT security landscape via unprecedented levels of connectivity and automation – complex Cyber-Physical Systems now operate across physical space to the Cloud, and beyond. Increasing digital transformation across industrial environments is leading to an increase in complex and diverse Cyber-Physical systems which are bridging IT and OT systems in an unprecedented way. As a result, and in equal measure, this is increasing opportunity and cybersecurity risk. Increased connectivity is accelerating industrial automation, but also exposing traditionally isolated systems up to the “outside world” (IT, IIoT, Cloud, remote access, Internet, etc.). Greater automation is helping to optimise processes, and at the same time increases the risk of cascading failure (in both directions), physical impact and safety incidents. Process efficiency and quality is leading to improved quality and value, while placing greater dependency on data-driven processes to deliver end-to-end supply chain and process execution. With the promise of cyber-physical systems revolutionising OT operations comes a missing link between IT and OT in how we monitor and protect them.
Challenges – OT security landscape
- OT environments often lack security controls and monitoring visibility that would be deemed a bare necessity for traditional enterprise IT networks.
- Industrial systems have a long operational shelf life, with devices and equipment remaining in operation for decades – leading to a large no. of legacy devices that are difficult or impossible to patch.
- Most OT/ICS are embedded platforms that support deployment agent of on-device endpoint security software. Meaning that system and machine activity visibility is severely limited.
- OT devices are connected on range of heterogeneous protocols, many of which are proprietary and insecure by design, and in many cases only well-understood by OEMs, Vendors, and Integrators. Meaning that emphasis on obscure protocol behaviours is challenging for both IT and OT teams to fully understand and respond to effectively.
- System faults, equipment malfunctions and cybersecurity threats can create equally disruptive impacts in OT systems. However, determining the root-cause of anomalies and high risk-system activity is challenging, due to a lack of holistic visibility at the cyber-physical level – across both operational network and physical process activity in unison. Today, IT teams are mainly limited to a partial view of the OT network, whilst OT teams focus on specific aspects of process monitoring. This means both technology, people and incident response processes in OT/ICS systems are fragmented and lack collaboration.
“In the realm of OT Security, a panoramic view is key. We must extend beyond traditional network monitoring, harness the potential of AI, and integrate the expertise of IT and OT teams. Only then can we optimize incident response and enhance operational resilience. This is the promise of Cyber Physical Detection and Response – a holistic approach to security in a hyper-connected world.”
“Beyond Network Monitoring: CPDR in Enhancing OT Security and Operational Resilience”
Today, OT Security narrowly focuses on network monitoring – this is only half the picture, and picture best understood and managed by traditional IT security teams. Resilient Cyber-Physical Systems require Cyber-Physical monitoring and AI. Cyber Physical Detection and Response (CPDR) transparently upcycles data from existing OT and IoT Machine-to-Machine APIs and seamlessly combines process and physical machine analysis with passive network monitoring, to deliver Cyber-Physical visibility. With this lens, AI automates detection and correlation of cyber and physical system alerts to determine root-cause (e.g., Threat, Fault, Failure), and respond in seconds. CPDR force multiplies and engages both IT and OT teams, optimising incident response by orders of magnitude – enhancing operational resilience at all levels.
The Solution
IBM and Exalens evolved the solution to address threat landscape affecting cyber-physical systems and bridged the technology and application gap left by most OT security solutions.
The resulting solution brought together the best of what IBM and Exalens each had to offer. The Cyber Physical Detection and Response (CPDR) is an agentless, protocol agnostic, lightweight and non-intrusive intelligent and automated solution that complies to NIST 5 pillar framework.
- Identify enables identifying critical CPS and OT assets and the cybersecurity risks that could impact them, including identifying assets that are essential to your organization’s operations such as control systems, manufacturing equipment, and sensors, and threats such as malware, unauthorized access, and physical attacks that could pose a risk to those assets.
- Detect enables detecting cyber-physical incidents so that you can respond to them quickly. Including implementing controls such as intrusion detection, monitoring, and auditing.
- Respond involves automated and orchestrated response to incidents to minimize impact.
- Recover involves recovery from incidents so that critical CPS assets are restored to normalcy. For CPS, recovery may include a combination of intelligent automated and manual process.
CPDR: A modular customizable solution to meet your specific requirement.
The identify and detect capability of the Exalens component of CPDR solution is designed to interact with the cyber-physical system for asset identification and anomaly detection. Exalens solution is fully integrated with the IBM’s entire threat management stack including QRadar SIEM, SOAR, XDR Connect Platform, QRadar Suite UAX and Log Insights using connectors such as UDI, CAR and DLC, applications such as AppHost, modules such as DSM and additional API and script connections.
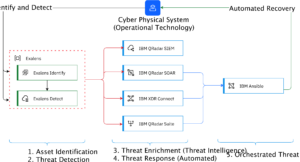
High-level architecture of the Cyber Physical Detection and Response Solution
IBM has configured and built playbooks with both IBM QRadar SOAR and IBM Ansible so that the threat response is automated as well as recovery from a fault, failure or threat can be orchestrated.
CPDR allows you to select and choose components that you would like to have to enrich, respond and recover part of the solution, to meet your specific business needs.
The Exalens platform learns your operational processes, analyses cyber-physical data, detects variations in behaviour, then correlates and classifies incidents to alert you in plain language about what, where, when, how, and why an event is impacting your operations and how to best respond. Using process monitoring, Exalens baselines and learns processes to supercharge the detection of threats, faults, and machine failures, so that the businesses can respond efficiently and effectively.
Identification
The Exalens system automatically discovers and classifies cyber-physical system assets and continuously tracks and profile their application, network, and process activity across the operations environment.
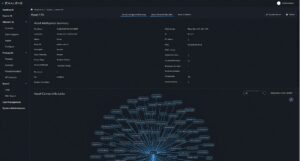
Screenshot of the Asset Information screen of Exalens Cortex that shows the asset identification capability.
Detection
Detect the root cause and the entire chain of impacted assets using Exalens AI analyst engine which classifies and correlates incidents to determine the source of threats and anomalies and provides complete activity details so that the businesses can respond quickly and efficiently.

Screenshot of the Source IQ Cascade screen of Exalens Cortex that anomaly detection in progress.
IBM threat management product stack is a modernised set of advanced and integrated products and services that helps organizations to detect, investigate, and respond to cyber threats. While Exalens system is best placed to identify cyber physical assets and detect cyber physical anomalies, IBM platform is a market leader for enrichment, response, and recovery from cyber physical events. The Exalens system has been integrated with IBM QRadar SIEM, SOAR, XDR Connect and QRadar Suite, so that customer can use existing IBM threat management solution to enrich, respond and recover from cyber-physical events without need to add additional components for the solution to work.
Response
IBM uses X-Force to enrich cyber-physical anomalies with threat intelligence insights (TII). The TII is available with both XDR Connect and QRadar Suite and separately integrated if the solution uses QRadar SOAR or SIEM only. Once the threat has been enriched the anomaly is responded using playbook configured in SOAR or case management and appropriate to the detected anomaly.
If the CPDR solution is configured with XDR Connect or QRadar Suite, then proactive threat hunt can be enabled to automatically search for indicators of compromise and hunt anomalies across your cyber-physical systems with limited of no involvement of your OT SOC or operations teams.
Recovery
The CPDR solution during the response stage automatically triggers Ansible if recovery is required. Ansible, using its rich and comprehensive playbook, could either trigger a fully automated recovery, which involves no manual intervention, or may trigger an orchestrated recovery where each step of the recovery process is manually reviewed by authorised individuals before the recovery action is taken.
IBM and Exalens each have unique capabilities for cyber physical systems. Exalens provides a solution for cyber-physical asset identification and anomaly detection, designed to address the challenges of the current cyber physical landscape, while IBM offers state-of-the-art threat enrichment, response, and recovery capabilities. The collaboration enabled both companies to build a unique end-to-end threat management capability for the cyber-physical systems which addresses strong demand from various sectors.
IBM Client Engineering’s Value Engineering Method
IBM Client Engineering was introduced to Exalens – a cybersecurity start-up via Plexal – a London based Innovation Consultancy for start-ups. IBM initiated the collaboration through an Ecosystem Development Programme to demonstrate that the collaboration between a start-up and an established technology provider would create tangible value and an innovative solution approach to solve a real-world business challenge for a government entity through a Proof of Value (PoV) approach. Exalens was selected to co-create with IBM Client Engineering and innovate on a ground-breaking area of cyber physical threat detection and response capabilities in the context of Operational Technology (OT), IoT and IT security and monitoring.
How did IBM Client Engineering approach the problem?
Testing hypothesis
Initially, IBM Client Engineering set out to test the hypothesis that by integrating Exalens’ cyber physical threat detection capabilities with IBM Security solutions to leverage incident response capabilities, we could develop a joint solution to address the PoV initiative and prove that the combined capabilities of Exalens and IBM meet the PoV initiative requirements.
We co-created with Exalens on a set of integrations that would result in a unified PoV of CPDR solution that can deliver an intelligent and automated cyber physical threat detection and response capability.
Firstly, case management scripting enabled Exalens to create, update and escalate incidents in IBM XDR connect. Secondly, a new AppHost was developed to integrate QRadar SOAR and XDR Connect Case Management with Exalens threat detection capabilities to deploy SOAR components such as custom fields and import functions automatically. In addition, UDI and CAR services connectors were developed. The UDI Connector was built to enable federated search of Exalens security data, and the CAR connector was designed to collect information about assets, users, and risk profile to generate insight about the overall risk posture.
After addressing the PoV brief for the Ecosystem Development Programme, the team was keen to take an IBM Design Thinking approach to gain more insight about how the PoV solution could work in context and help define the value proposition of the integrated cyber physical threat detection and response capabilities.
We collaborated with the IBM Design team through a series of value proposition workshops to align on the Opportunity Statement, create a series of Empathy Maps for user profile groups such as Operational Technology, Business, SOC engineers then explored a series of use cases relating to both the cyber physical detection and response capabilities of the PoV solution. Through this exploration process we realised there was multi-industry application for the solution that we had built and that we had defined a ground -breaking cyber physical detection and response (CPDR) architecture.
“Cyber-Physical Detection & Response is the next paradigm shift in OT security, seamlessly unifying device, network, and physical process monitoring to automate root cause analysis, spot and respond to cyber threats, faults, and machine failures in seconds.
What’s Next?
Learn how IBM Client Engineering can help you rapidly innovate to solve your business challenges.
Learn how IBM Security QRadar EDR solution can help your business stay ahead of cyberthreats.

Ryan Heartfield
CTO and Co-Founder, Exalens
More Security stories
By Col Chambers and Ed Gillett on 5 February, 2025
Preparing for the defence of the Realm
In light of current conflicts, the UK is now faced with real-world military decisions that will affect our immediate future. Ed Gillett and Col Chambers assert that industry and government must switch to a readiness mindset before the European post-war peace shatters. “My vision for the British Army is to field fifth-generation land […]
By Juan Bernabe Moreno and others on 12 December, 2024
Frontier Fusion: Accelerating the Path to Net Zero with Next Generation Innovation
Delivering the world’s first fusion powerplants has long been referred to as a grand challenge – requiring international collaboration across a broad range of technical disciplines at the forefront of science and engineering. To recreate a star here on Earth requires a complex piece of engineering called a “tokamak” essentially, a “magnetic bottle”. Our […]
By Nick Levy on 9 December, 2024
Safer Technology Change in the Financial Services Industry
Many thanks to Benita Kailey for their review feedback and contributions to this blog. Safe change is critical in keeping the trust of customers, protecting a bank’s brand, and maintaining compliance with regulatory requirements. The pace of change is never going to be this slow again. The pace of technology innovation, business […]































