Perspectives
Are you keeping pace with evolving threat landscape?
27 June, 2023 | Written by: M A Shaikh, Julia Rodgers, and Ryan Heartfield
Categorized: Perspectives
Share this post:
There is no doubt that the endpoints are under attack.
83% of organizations studied have had more than one data breach according to IBM’s Cost of a Data Breach report 2022. With 84% of security professionals believing that most attacks will start with the endpoint, means that the endpoints continue to remain the primary attack vector.
Breaches happen most often at the tool we use the most, which is at the endpoints. This can refer to laptops, workstations, or devices. This might happen when users accidentally click on a malicious web link or open an infected file, which starts a process at the endpoint. This can potentially disrupt business continuity when cyberthreats are not detected or mitigated efficiently. Once attackers gain access at the endpoints, they might be able to move through the infrastructure looking for its ‘crown jewels’, an organization’s sensitive, important data.
A rise in—and complexity of—malicious and automated cyber activity, most of which originates at the endpoints, has led to the struggle with evolving endpoint threats today. Endpoint attacks are on the rise, with new cyberthreats and ransomware attacks emerging daily.
Alarmingly, attacks are also increasing in sophistication.
Mckinsey writes that “Hackers are using AI, machine learning, and other technologies to launch increasingly sophisticated attacks” in an article. – Cybersecurity trends: looking over the horizon (2022). This megatrend is here to stay as attackers become more skilled at targeted attacks.
For example, there has been a reported 146% increase in Linux ransomware with new code, indicating ransomware innovation, ref: (IBM Security X-Force Threat Intelligence Index 2022)
Cyber adversaries are also increasingly making use of techniques like ‘living off the land’, manipulating legitimate software and files to disguise their presence and making it harder for security teams to stay ahead of attackers.
“Protecting the endpoint estate remains a challenge for organizations in light of more attacks, which are faster and more sophisticated.”
This is further compounded by a worldwide shortage in cyber talent.
Challenges continue to mount for security teams to stay in control (manage and secure) over these ever-growing security workloads. Workloads are growing: According to a research conducted by ISSA 62% of cybersecurity analysts are experiencing increasing workloads, while burnout among security staff was reported to hit a high of 38%. Inexperienced, new, and fatigued analysts also struggle with complex tooling, alert overload, and time-consuming investigations.
As attacks becomes more complex, security teams can also expect to sieve through significantly higher amounts of data to find anomalies and to determine if such anomalies are a real attack. This comes as IBM’s Institute of Business Value trend report for 2023 revealed that 54% of executives say a lack of talent is one of the greatest obstacles to their organization’s cyber resilience.
How can organizations continue to keep pace with the evolving threat landscape and the growing number of attacks?
It is now time to rethink endpoint security.
Businesses are faced with a balancing act: how to stay in control of data and business growth, while ensuring their business continuity in case of cyberattacks directed at the endpoints?
Tackling modern endpoint challenges requires modern solutions so organizations can move from a reactive to proactive security posture.
Staying ahead of attackers begins with leveraging smart automation and tools:
1. Behavioural analytics must move beyond signature-based detections.
Relying on just a signature-based approach is not enough to safeguard against “unknown” endpoint threats. A behavioural-based approach is needed to spot anomalies when there are deviations from the norm, especially in the age of zero-day attacks especially when it comes to previously unseen threats.
2. Easy UI, easy to use visual workflow, and integrated analytics and response workflow.
The challenge is being unable to identify the attack or get to the root cause quickly to remediate threats. A concise, clear graphical overview of a threat hunt / attack visualization enables fast triaging for analysts to do efficient work.
3. AI & Automation, Autonomous response capabilities
Attack speeds are accelerating, leaving little time for human analysts to react. Leveraging smart automation helps put analysts back in control by enabling teams to understand threats briefly and triage incidents quickly. With an AI-driven EDR, human analysts no longer must sift through alerts manually. Instead, a modern EDR automates detection and response, so that businesses can respond automatically in a matter of seconds. As security automation is not reliant on malware signatures, malicious processes can be automatically terminated upon detection. Having immediate attack identification is crucial to successfully stop an attack and reduce the recovery costs involved in a breach.
4. Proactive threat hunting, discover hidden threats for a clean environment.
Due to the lack of visibility, how can organizations remediate threats (including dormant and persistent threats) in case of a breach? A modern EDR can automate threat hunting, enabling analysts with granular search parameters to weed out persistent and dormant threat entirely.
Why Endpoint Detection and response?
Let’s do a deep dive into capabilities that differentiates EDR from traditional endpoint protection.
Firstly, security teams should be wary of the false sense of security that comes with traditional endpoint protection measures, like antivirus solutions, as they are no longer enough to defend against ransomware and other complex, automated attacks.
Organizations that rely on legacy approaches find that they have poor visibility, as such methods rely on finding what is known (signatures), but attackers utilize unknowns (fileless/ransomware attacks).
When dealing with complex, unknown threats, ask yourself these things:
- Would you know when you have been breached?
- Would you know if an attack was taking place right now? (Includes lateral movement or in-memory attack detection and more)
- If you did detect a breach, would you be able to return to a safe and normal operational situation? – with persistent threats and other Indicators of Compromise (IoC’s) removed?
If any of these questions is answered with a no, it is perhaps time to seriously start looking at EDR.
EDR vs. Traditional Endpoint Security
With attackers moving faster than before, organizations need to look at new and innovative ways to stay ahead of the steep increases in attack sophistication, while protecting their sensitive data.
EDR uses real-time analytics and AI-driven automation to protect against cyberthreats that would otherwise get past AVs and traditional endpoint security.
EDR’s threat detection, analytics and automated response capabilities can identify and contain threats that penetrate the network perimeter before they can do serious damage. EDR also provides tools that teams can use to discover, investigate, and prevent suspected and emerging threats.
IBM Security QRadar EDR
Built by an elite group of cyber security experts and AI/ML researchers, IBM QRadar EDR was designed by analysts, for analysts and has been recognized for its new approach in the industry.
IBM QRadar EDR was recognized by the following industry experts and renown research firms:
Funded by the European Union, IBM QRadar EDR was also awarded the seal of excellence by the EU, and recognized as an innovative cybersecurity solution that can detect and immediately respond to attacks that are highly sophisticated and damaging.
IBM QRadar EDR is also recognized by Forrester and IDC and has won multiple awards and accolades.
IBM QRadar EDR is also consistently tested against real-life attack scenarios and in 2023, IBM QRadar EDR successfully completed its 4th round of the MITRE Evaluations, with a focus on Turla.
Endpoints remain the most exposed and exploited part of any network.
The rise of malicious and automated cyber activity targeting the endpoint leaves organizations that rely on traditional endpoint security approaches struggling against attackers who exploit zero-days with ease and launch a barrage of ransomware attacks using automation. The volume of alerts is leading to fatigued analysts struggling with complex tooling, alert overload, and time-consuming investigations that are often manually done. IBM QRadar EDR, remediates known and unknown endpoint threats in near real-time with easy-to-use intelligent automation that requires little-to-no human interaction. You can make quick and informed decisions with attack visualization storyboards and leverage automated alert management and advanced continuous learning AI capabilities.
There are some key differentiators I want to draw attention to:
- First, a Clear Line of Sight. You can regain full control over all endpoint and threat activity from heightened visibility across your environment. Designed to be undetectable by adversaries, NanoOS technology operates outside the operating system, and provides deep visibility and protection into the processes and applications running on endpoints.
- Next, IBM QRadar EDR helps you Automate Your Response. With continuously learning AI, detect and respond autonomously in near real-time to previously unseen threats and helps even the most inexperienced analyst with guided remediation and automated alert handling.
- Next, moveFrom Reactive to Proactive and get ahead of attackers with easy-to-create detection and response use cases that return results in seconds. Easy to build use cases are deployed across the organization without interrupting endpoints uptime.
- And finally, check out the most recent MITRE ATT&CK evaluations. IBM QRadar EDR has continued to outperform over the past years, and it brings to life the value of our solution.
Why endpoint detection and response are so critical to stay ahead of attackers?
To illustrate the accelerating attack speeds and see IBM QRadar EDR in action against a real-life attack, read about the early detection of zero-day threat Quantum Locker Ransomware with QRadar EDR.
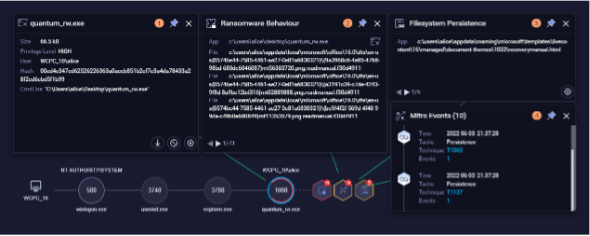
QRadar EDR’s behavioral tree shows how Quantum Locker Ransomware (RaaS) was detected and actively mitigated in near real-time.
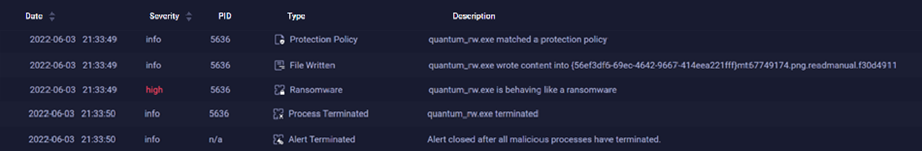
Upon detection, QRadar EDR terminated all malicious processes involved before Quantum Locker was able to cause harm.
Quantum Locker first appeared in August 2021 as a rebrand of the Mount Locker ransomware.
For some context, ransomware attacks usually begin with threat actors obtaining access to victim machines by deploying various TTPs to advance in the kill chain before ransomware is executed.
Typically, there may be significant delays between a given threat actor first gaining access to a target machine and the detonation of the ransomware. Threat actors employ varying TTPs to gain access, conduct lateral movement, and escalate privileges before ransomware can be effectively deployed.
What sets Quantum Locker apart from other ransomware strains is its speed of attack, in taking less than 4 hours from initial access to the victim machine before executing Quantum Locker domain wide. This was noted in The DFIR Report as “one of the fastest ransomware cases observed.”
Unique EDR challenges of a fast-growing tech startup.
Exalens, one of the fastest growing tech startups working with regulated, government, and critical infrastructure companies had additional complexities and challenges with their endpoint security. With highly diverse and heterogenous IT environment, lack of both resource and expertise, exposure to advanced threats and threats, zero-day exploits, impending compliance requirements, Exalens needed an EDR solution that can support its small but growing endpoints with the agility of a startup.
Working with IBM Client Engineering
Exalens team noted that “from the moment we expressed interest in IBM QRadar EDR as a solution for our endpoint security, the IBM UKI Client Engineering team went above and beyond to help us”.
Looking back at the challenges Ryan Heartfield, CTO and Cofounder of Exalens said “A huge blocker for us had been the small scale whereby trying to find a suitable solution that covered our diverse systems while addressing unique challenges we presented, was very difficult with other vendors”.
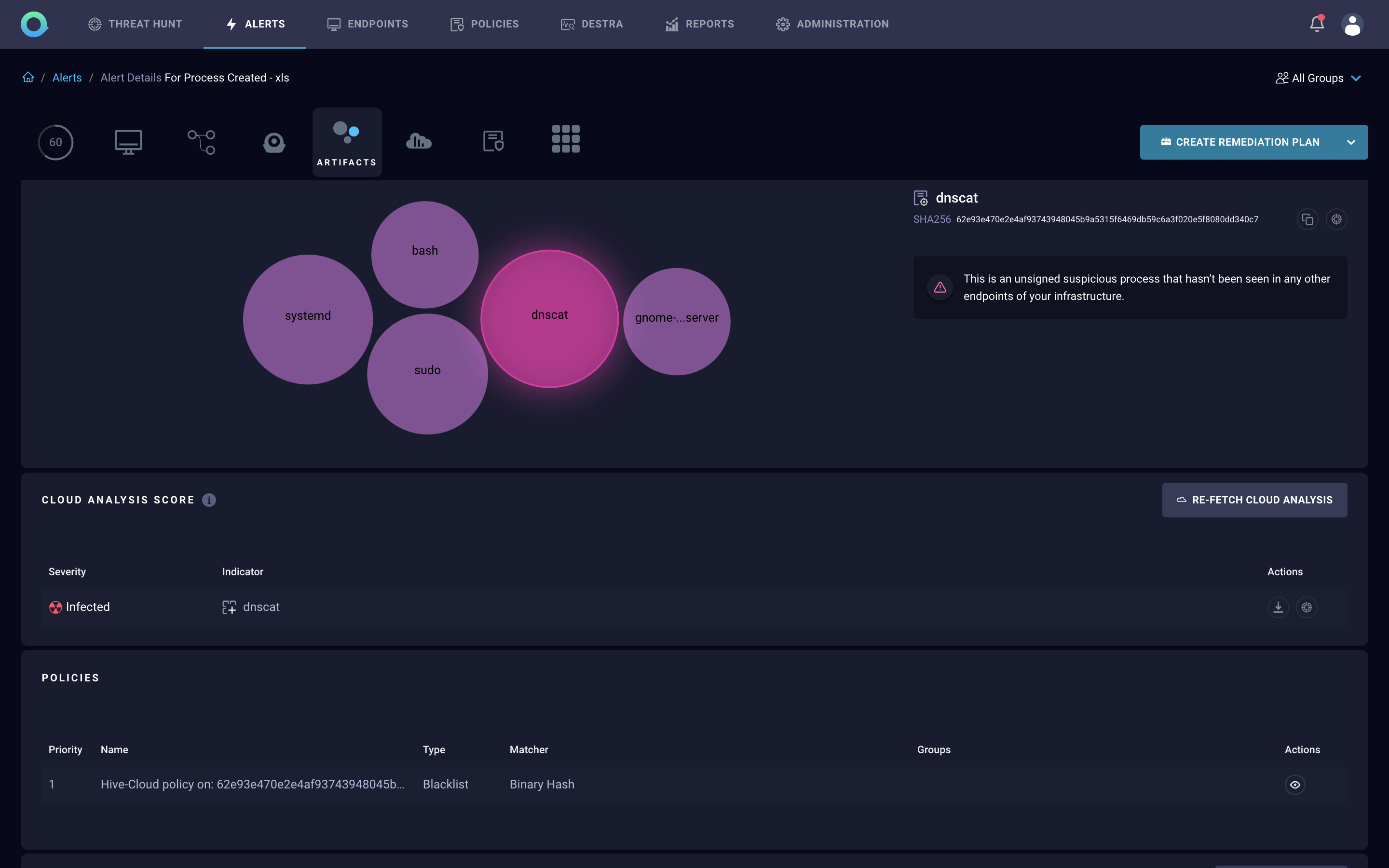
Screenshots are of alerts on IBM QRadar EDR that Exalens generated during its internal penetration test and/ or other simulations.
When asked how IBM UKI Client Engineering approached the problem he said “Regardless of size, the IBM Client Engineering drove at an unbelievable pace, with exceptional levels of engagement our ability to get exposure to the platform, find a suitable partner that could deliver the solution, as well as taking care of the entire MVP process without any heavy lifting on our end.
Ryan continued “Practically, this resulted in feeling like we were really be taken care of by the Client Engineering, particularly by Manjer, who was superb and instrumental in delivering the MVP process end to end within a few weeks. We are truly grateful for that and must say our experience has been incredible. IBM Client Engineering teams were transparent about the technology, its capabilities and USPs, which showed a great level of integrity that helped to build trust with customers that decides to onboard an EDR solution that has such an important role in securely enabling the business.”
Talking about IBM QRadar EDR.
One of the unique experiences we had with IBM QRadar EDR MVP was the feeling of being a part of the journey, and not only as a customer, but contributing directly. Often this engagement feels and plays out like a one-way street – but we felt that our views both operationally and technically were really taken onboard and utilized internally such that it provided value and impact to both parties.
We felt that we really co-creating the solution to engineer it to our requirements, and this was brought home by a fantastic workshop with Julia, Manjer and the design team that help us focus really what we were looking for, how the solution could enable our business and under what parameters success looked like for us. At first this was high level, but co-creating with the team helped us really pinpoint what it is we needed and cared about.
As a result, the MVP has provided significant value and impact in improving our security posture, as well as helping us with compliance requirements. Aside from feeling that the team was only a phone call / email away, the results of the MVP for IBM QRadar EDR were impressive, it produced 0 false positives during our testing, and worked reliably on all our platforms. It is a superb EDR platform that meets the complex requirements or our diverse start-up estate, without introducing a higher workload to our small team, without requiring a constant security team to administer it.
How is your experience since buying the solution?
IBM QRadar EDR has proved to be a transformative capability in our cybersecurity posture and operational resilience. Not only do we now feel correctly equipped to tackle threats that come with doing business as a cybersecurity vendor, or indeed, operating in the digital age. But in equal measure, we have the comfort of knowing that even as a SME, we have the right AI technology capable of effectively and efficiently intercepting and mitigate threats to our systems at machine-speed. Having that kind of comfort in today’s cybersecurity landscape is rare I would say.
Are you equipped to stop zero-day (unknown) threats like Quantum Locker ransomware?
Client Engineering: Investing in our clients’ success.
It was not Exalens first interaction with IBM UKI Client Engineering, having previously collaborated on the innovative CPDR initiative. Exalens reached out to the UKI Client Engineering with their challenge of finding modern endpoint detection and response solution that would also meet the complexities of a scaling start-up. Exalens, given their presence in the industry and cybersecurity expertise, were fully aware of IBM QRadar EDR and were optimistic that it will meet their endpoint security requirements.
“Exalens wanted to rapidly innovate and co-create with IBM Client Engineering to solve their unique, complex endpoint security challenges.”
IBM’s first call to action was to demonstrate the IBM QRadar EDR to Exalens to ensure that the solution met the requirement of the customer before any further time or cost investments were made. Fully satisfied with the product demonstration, Exalens next wanted to experience the EDR solution within the complexities and limitation of their environment to determine if the solution addresses unique challenges of their business. IBM, aware of the deadline that Exalens was pursuing for completing all processes needed to start work with Client Engineering, in less than 5 business days.
Exalens then embarked on the Client Engineering journey which takes a customer through the Value Engineering method to determine specific use cases and corresponding success criteria, followed with technical specifications of the solution and finally co-creation of the MVP in iterations.
IBM Client Engineering’s Value Engineering Method
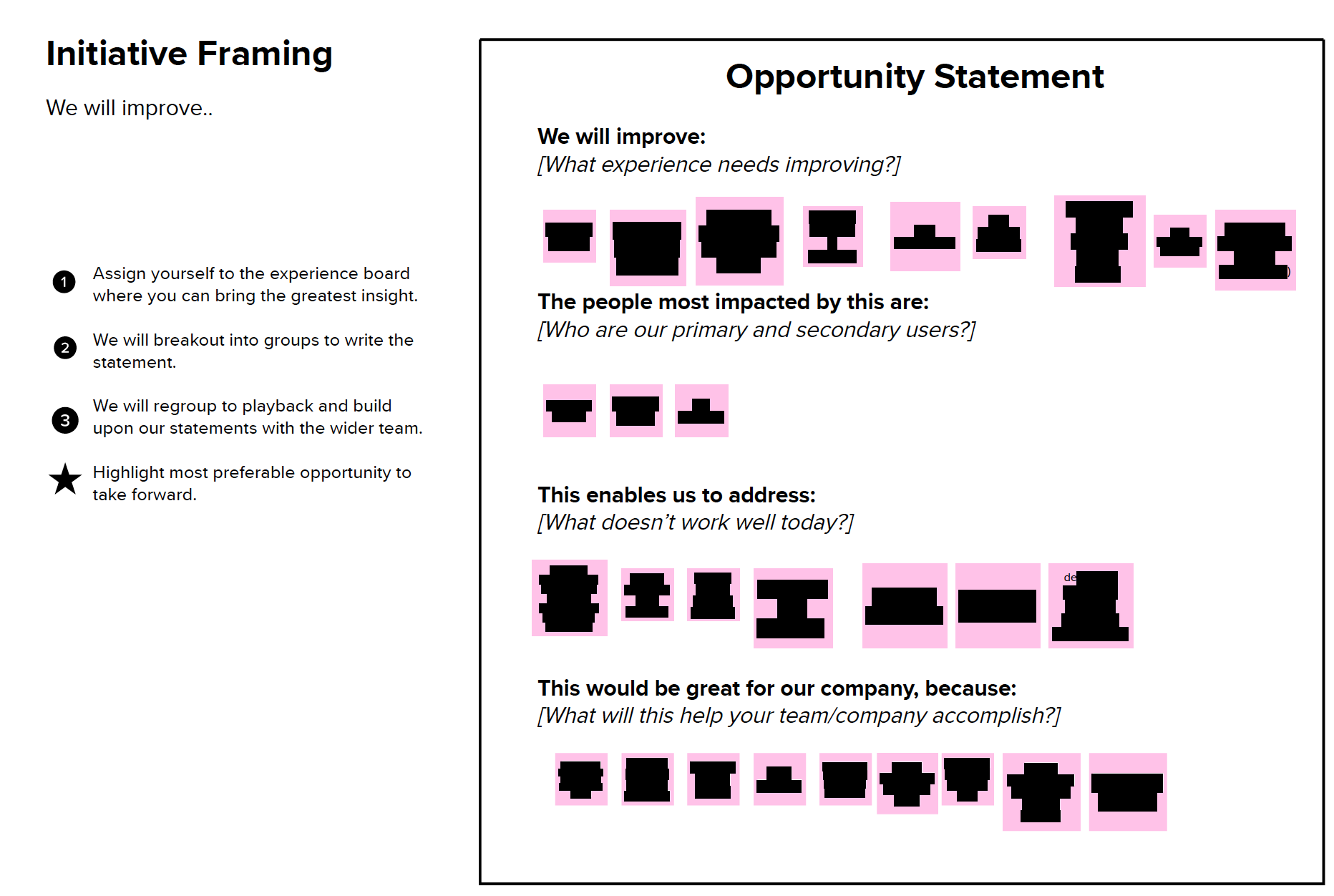
The Value Engineering method enables IBM Client Engineering to address the customer’s business challenges using mature and proven technology solutions but with an agility and innovation of a start-up. The Value Engineering method has four distinct phases, starting with innovate, which allows us to explore opportunities and scope a “Proof of Value”, leveraging multi-disciplinary experts. Once the value is defined, the process moves to the prepare stage to get everything in place for a rapid build. The next stage in the process is co-creation during which IBM Client Engineering builds the scope and fulfils the success criteria, validates, and improve over a series of sprints and playbacks. Finally, IBM builds the plan and engages the team to transition the MVP to production.
“IBM Client Engineering leveraged its unique Value Engineering methodology to go from the initial phase to transition stage in less than 2 weeks.”
Client Engineering conducted one workshop during the innovate phase, to understand user needs, refine the business opportunity, identify IBM’s technology point-of-view and accelerators, design a joint solution to validate, architect the technical components, and define use cases and success criteria.
Using Mural to collaborate, Client Engineering pursued activities such as definition of opportunity statement, identifying assumptions and risk, prioritisation of assumptions and risks and testing of the riskiest assumptions, which defined that the MVP use cases must demonstrate the following.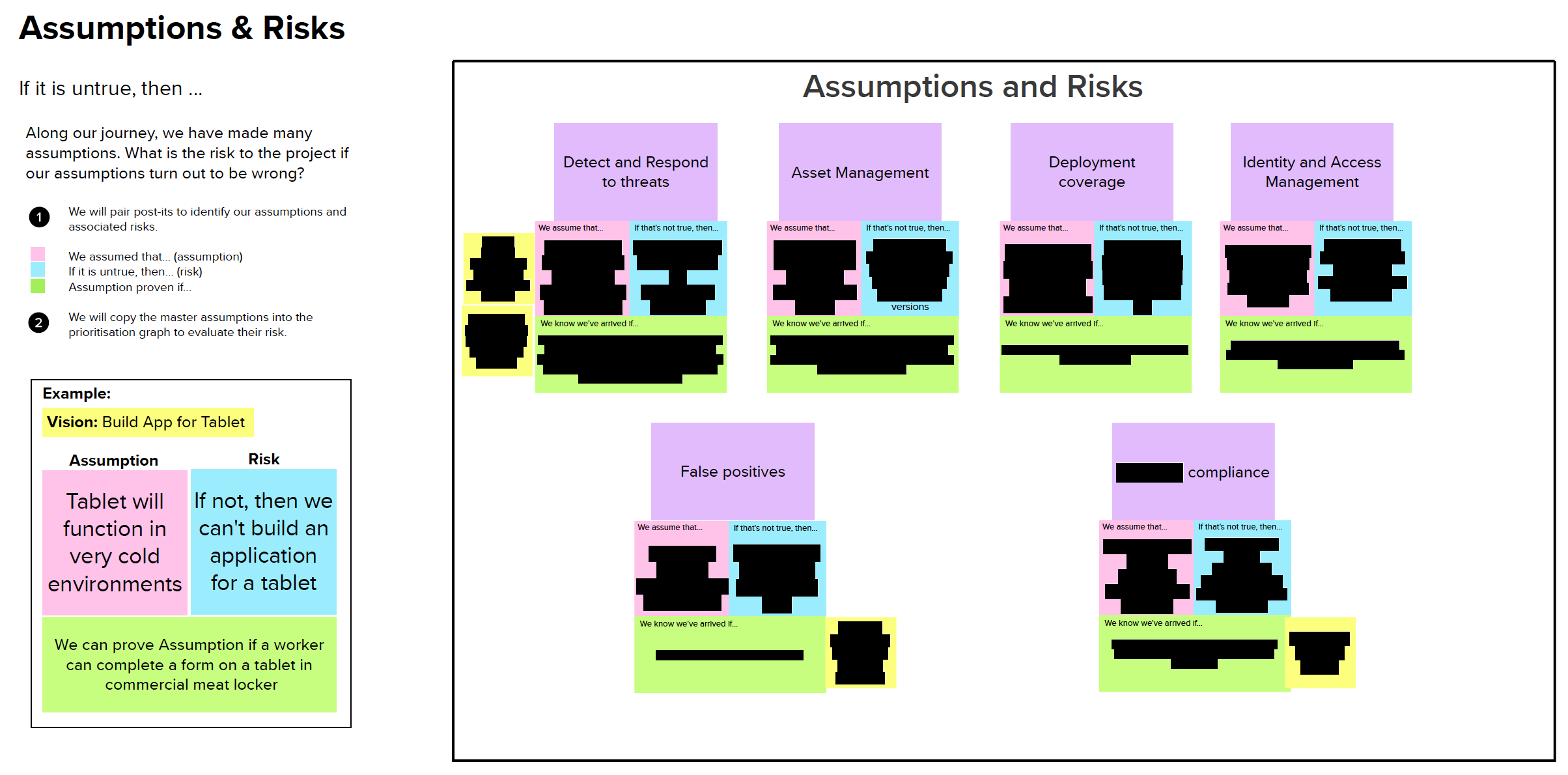
- Complete visibility and protection into the processes and applications running on endpoints.
- Intelligent automation of detection and remediation in real time with minimum intervention.
- Behavioural analytics to detect anomalies that deviate from normal.
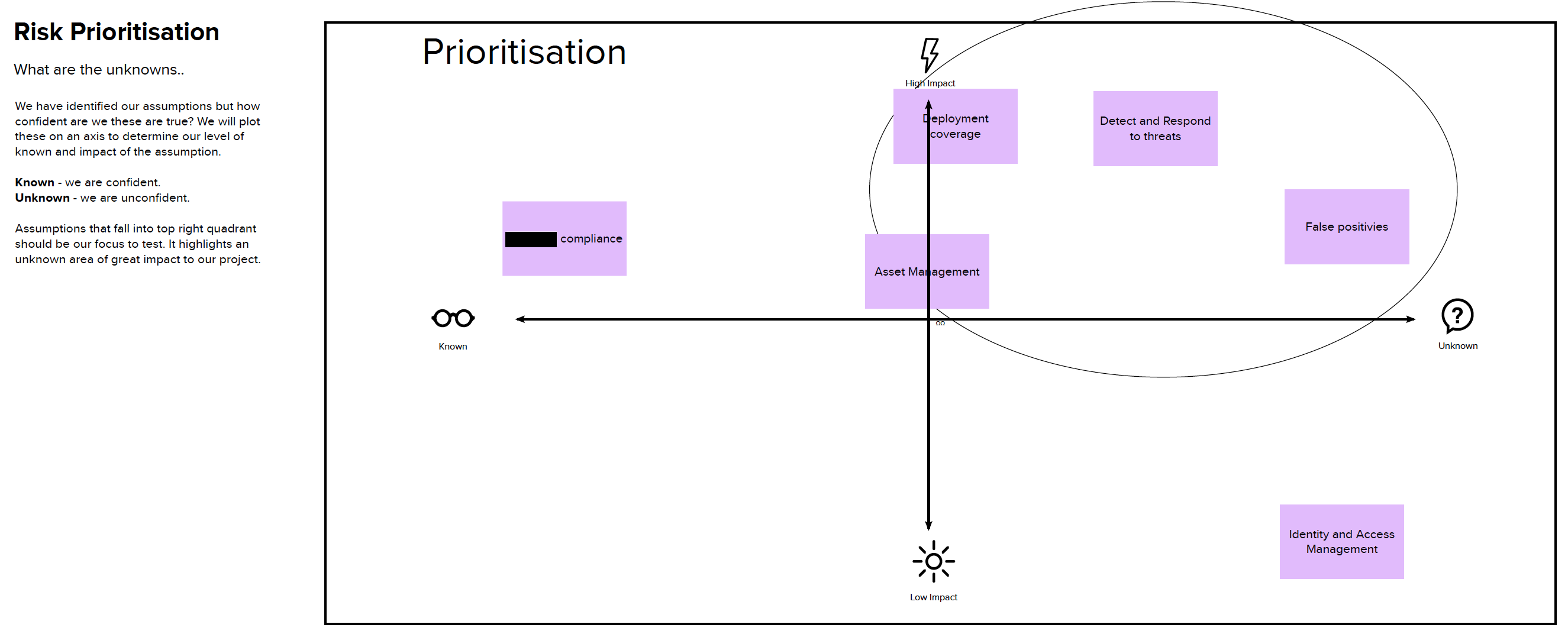
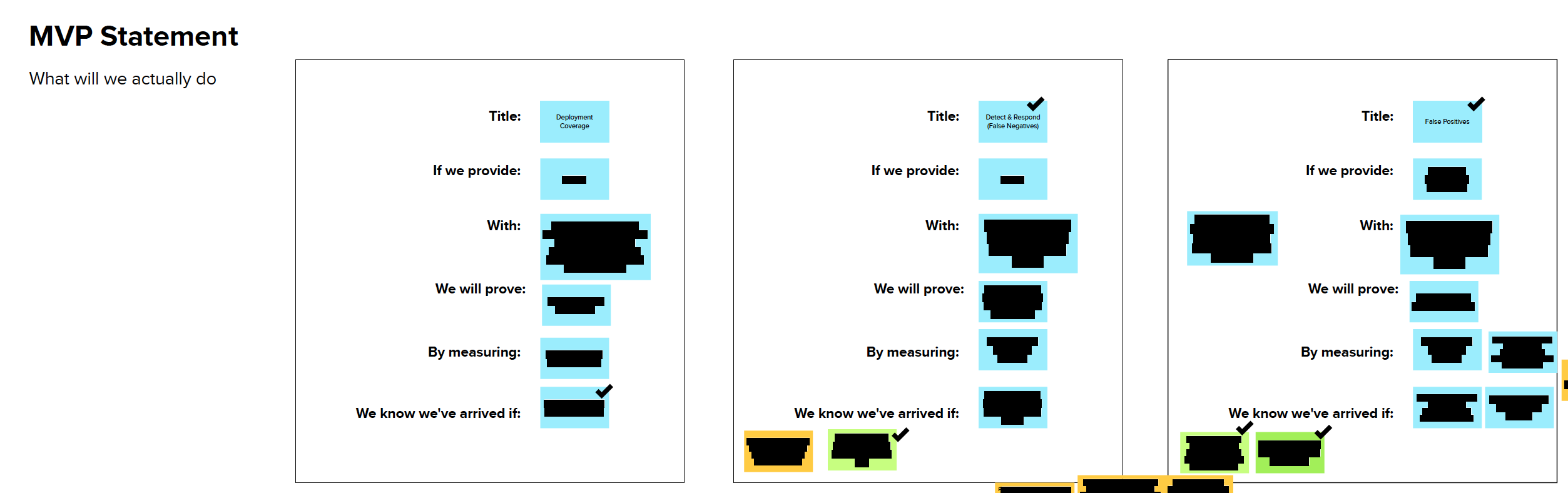
Client Engineering and Exalens agreed that if the proposed MVP met the following success criteria, within the MVP test duration of 2 weeks, the IBM QRadar EDR MVP could be considered a success.
- Complete endpoint deployment coverage
- Automated detect and response with no false negatives.
- Low or no noise (False Positives) with the platform
IBM demonstrated that the MVP met the defined success criteria in less than 7 days.
Exalens was pleased with the outcome of the MVP and transitioned the MVP into a full deployment the following month and since then IBM QRadar EDR has been helping Exalens keep pace with the evolving threat landscape, meet compliance requirements and not worry about its endpoint security.
What’s Next?
Learn how IBM Client Engineering can help you rapidly innovate to solve your business challenges
Learn how IBM Security QRadar EDR solution can help your business stay ahead of cyberthreats

CTO and Co-Founder, Exalens
Transforming B2B Sales: Unleashing the Power of AI and Automation in Telecommunications
In the dynamic world of telecommunications, staying ahead requires constant innovation. VMO2, a renowned leader in the field, recently embarked on a journey to evaluate latest technology as an opportunity to enhance end-to-end customer experiences and automate low-value tasks within their B2B sales process. The aim was to achieve time and cost savings, while improving […]
New milestone for IBM-AWS partnership makes it even easier for clients in the UK to buy IBM software on the AWS Marketplace
Last summer, IBM launched a programme that enabled UK clients to purchase IBM software on the Amazon Web Services (AWS) Marketplace. Ever since it has given our clients the ability to recapture at-risk spend with AWS, simplify their procurement process, and improve time to deployment. Given the positive response from clients I’m pleased to announce […]
The Six Reasons Why Apprenticeships Mean Business
As a passionate champion of apprenticeships, I’m delighted to see the model growing in popularity and reputation. UCAS, for example, now features apprenticeships on their website on a par with traditional university opportunities. Despite this, however, I’m often still asked “can we have a graduate for our business?”. To which I reply: “how about an […]




