security
Ransomware attacks levels up, again!
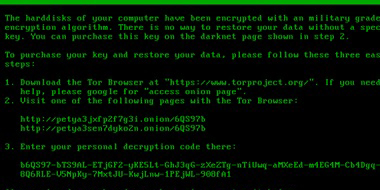
Remember WannaCry? When a group of unknown threat actors carried out one of the largest ransomware attacks of its kind, hundreds of thousands of computers in 150 countries got infected. Wannacry hit the news barely a month ago! Fast forward 1 month…Yesterday, newsmedia around the world reported on a similar attack with ransomware called Petya. […]
Redefining Business and Security. Come see us at the Watson Amsterdam Summit on June 14
Cognitive technology is transforming sectors, companies and professions – and it’s happening right now! On June 14, at the Watson Amsterdam Summit, we’ll be taking a very close look at what this means for security. As a CISO you need to help facilitate innovation, right? You cannot watch and wait, while your competitors press ahead […]
Watson and Cybersecurity: The big data challenge
Security is increasingly seen as a big data issue. The challenge these days is less about noticing that something isn’t right. The security landscape in 2016 was rocked with over 4 billion compromised records exposed. X-Force observed that tried and true methods like SQL injection, brute force attacks, malware toolkits and ransomware continue to be […]
On the password paradox and authentication innovation
Chances are that the device on which you’re reading this blog was accessed through one form of authentication or the other. One of the most wide-spread of those methods are passwords. They’ve become such an integral part of our lives that we often don’t think about them anymore. However, danger lurks right around the corner […]
Corporate data on mobile devices ‒ how do you stay in control?
Snack supplier Van Geloven also produces mobile bites Mobile devices – even companies can’t do without them anymore. But does all the corporate data on these data carriers have watertight security? Dutch snack producer Van Geloven has solved this with IBM MaaS360 Enterprise Mobility Management (EMM). And Van Geloven has shown that EMM doesn’t have […]
What to expect from the GDPR readiness assessment
Is a mild sense of panic taking hold of some of your colleagues? The implementation of the long-awaited General Data Protection Regulation (or GDPR) is inching closer and closer, and discussions will invariably revolve around: “Where to start?”, “Where to go?”, “What will it cost?”. If you attend any GDPR event, typically everyone, no matter […]
Hi, I’m Watson, and I’m the new security guy!
Voor bedrijven wordt het steeds moeilijker om zich tegen cyberdreigingen te beschermen. Bovendien laat een goede dief maar weinig sporen na: de oorzaak van een effectieve aanval opsporen is zeer tijdrovend en complex. En dan zwijgen we nog over het berekenen van de impact op je bedrijf. Nieuwe technologieën zoals artificiële intelligentie spelen een sleutelrol: […]
Seven Data Breach Lessons from research studies: What does a data breach cost?
Two questions keep coming back when I meet customers and partners in GDPR-related sessions. First, when it comes to preparing for GDPR: where to start? Second, what is the true financial impact of a data breach? On the first topic I recently started a blog series where we break down GDPR in nine digestible use […]
Why security needs to involve the Cloud
The days when the boundaries of corporate networks were clearly defined, are over. This is one of the starting points of IBM’s approach to IT security in the cloud. The reason being that the cloud enables you to better control the increasing complexity of IT systems and their security. According to the recent Forrester report, […]