Security
IBM Security Summit: Security Innovation Needs New Era Rethink
October 29, 2019 | Written by: 小編 / Editor
Share this post:
Innovation and security are entwined. Sustainable innovation needs robust security, while security needs innovation to tackle evolving threats. It was the main takeaway at the IBM Security Summit titled “Security for Innovation. Innovation for Security.”

Ngai believed that information security needs innovation to address new threats.
In his opening remarks, Francis Ngai, General Manager, IBM China/Hong Kong Limited, observed that companies are investing a lot into emerging technologies, such as artificial intelligence, big data, and cloud. Yet, these technologies increase the complexity of the operating environment and need hard-to-find talent. Lack of resources can increase the risk of and expose vulnerabilities that in turn can devastate bottom lines. The answer lies in making innovation and security to work together efficiently.
Data breaches are also becoming more expensive. A recent study by IBM and the Ponemon Institute on global corporate information security revealed that every enterprise data breach sets a company back by US$3.9 million and involves 25,000 records. It is also taking longer to identify and mitigate breaches. The research showed that it takes up to 279 days on average to identify and contain a single one (see graph). The unbelievable yet true numbers show that companies need to get serious on mitigating and handling security threats.
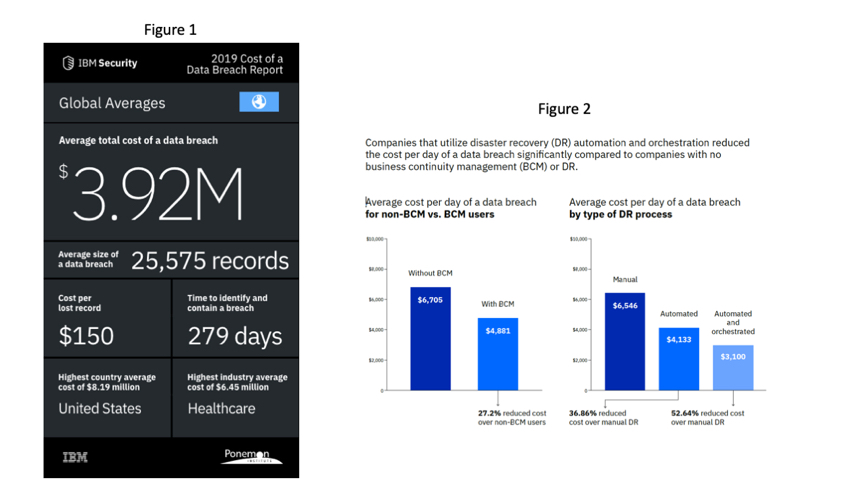
Figure 1: Key shocking figures from data security incidents. Source: 2019 Cost of a Data Breach Report; Figure 2: Companies that utilize disaster recovery automation and orchestration reduced the cost per day of a data breach significantly. Source: 2018 Cost of Data Breach Study: Impact of Business Continuity Management.
Paul Griswold, Executive Director for Product Management and Strategy at X-Force Threat Management, noted that cloud computing is one factor for rising threat levels. It introduces new enterprise operating models as data, applications, manpower, and other resources migrate to the cloud. But, enterprise security needs to catch up. He argued that companies should set up new policies and processes for application development, network monitoring, policy formulation, etc. to secure their cloud platform.

Griswold wants companies to address three aspects when addressing information security: culture, control, and chaos.
Three aspects for protecting cloud architectures
In his presentation, Griswold highlighted three aspects of information security for the cloud-based architectures: culture, control, and chaos. To be effective, companies need to build a security-minded culture. It includes C-suite, IT, and security teams working and communicating closely. For control, Griswold felt companies need to stop solely focusing on keeping out threats. He felt that threat in these innovative services and applications . A more effective way was to use “guard rails” or secure channels for transporting data between locations while monitoring behaviors of users, systems, and applications.
When it comes to chaos, Griswold believes companies need to embrace it as they work with multiple cloud providers and security tools. An integrated platform like IBM Security Connect can use artificial intelligence to manage and analyze this chaos for threats, highlight the risks inherent in different clouds, and help select the right security tools. Such a platform can also improve the overall security readiness of companies.
During the panel discussion, two representatives from HSBC and JETCO discussed with IBM security experts on how to prevent data leakage. Their views echoed Griswold’s.
Jacen Loke, , saw value in awareness training to educate employees on the various security threats within the company. He also advised companies to have robust controls and code of conduct to minimize data leakage due to human error.
Scrutinize security in new products and services
Matthew Shriner, the global SIOC Partner at IBM Security Services, agreed with Loke. He pointed out that to prevent data leakage, the most basic security measures must be deployed first. These include continuous detection of internal and external threats, timely updates, and warnings about intrusions. He also believed that many of the products developed by startups claim to have revolutionary features but are often only at the “minimum viable product” stage. So, these may have potential security risks, and it is up to companies to evaluate security worthiness when purchasing them. He also advised to get the CISO involved in such procurement decisions earlier to reduce risks.
The discussion then looked at the rise of the API economy and its impact on security. All agreed that while APIs allow the sharing of vast amounts of useful data, but they also wanted companies to understand that these opportunities come with risks. They argued that companies should look at strengthening their weakest links.

Panelists discussed the rising importance of information security. From left: Jacen Loke, Rex Liu, Matthew Shriner, Anurag Kuthiala, and Joseph Wong, Global SIOC Associate Partner, IBM Security Services.
Rex Liu, Director, Security Management at Joint Electronic Teller Services Limited (JETCO), shared that his company’s ATM and Open API platforms bring together a large number of banks and other business partners, and needs to stay highly vigilant for cybersecurity at each network node to proactively detect all kinds of potential threat. To achieve these, Liu and his team need to work with various external security technology partners. This cooperation will allow JETCO to implement the latest and most suitable technologies for defending against evolving cyberattacks. JETCO runs a cross-bank ATM switching service, and also provides new value-added services and inter-bank solutions to banks and other industries.
Pay more attention to disaster recovery
Anurag Kuthiala, Executive Solutions Leader, Europe, Asia Pacific, Greater China Group –Resiliency Orchestration at IBM Global Technology Services, emphasized that disaster recovery measures are becoming vital in a complete cyber resilience lifecycle as security breaches become more common. While prevention is the best cure, organizations have to also focus on the cure as well. They need to have a recovery strategy to minimize the impact of cyber breaches. Such a strategy needs to address three elements. First, copies of critical and confidential data as well as configuration items, which Kuthiala called as the crown jewels, must be periodically stored on a secure storage. Second, these copies must be validated for cleanliness, so organizations will have a ready list of clean copies for quick recovery. Third, organizations need an efficient tool to manage this process for governance and rapid recovery.
All panelists agreed that technologies such as artificial intelligence and automation are to information security. Companies have more tools and solutions to choose from than before. However, IBM’s Shriner stressed that companies based on the latest trends or to address incidents that just occurred. Instead, building a comprehensive security strategy and processes should be the initial step.
Get more tips and insights from the experts at the IBM Security Summit, or learn about the latest trends and trends in information security by visiting IBM Security Summit website. You can also download the research studies mentioned above by the Ponemon Institute for your reference at the below links:
科技工具非萬能 智能工作流如何為嶄新商業模式領航?
(文章於2021年8月28日在香港經濟日報網站刊登) 新冠肺炎疫情衝擊全球經濟,逼使各行各業加快數碼轉型(Digital Transformation)及嶄新商業模式,各種創新科技也因此加速普及。個別科技工具或許能助企業暫時減輕負擔或紓解燃眉之急,但它們並不是萬靈丹。 舉個例,企業可以運用人工智能分析產品銷售的狀況並藉此作出改善建議;但要真正收效,企業就必須根據這些分析和建議,持續地改革產品研發、製造以至物流等環節。要真正發揮創新科技的效力,智能工作流(Intelligent Workflow)的革新才是關鍵。
How HKTDC Reimagined Digital Sourcing In The Cloud
The vulnerability of supply chains was put on full display when COVID-19 struck. It exposed the risks of global interdependence and the fragility of global supply chains.[1]
Laying the Digital Foundation for Becoming an Innovative Insurer
How IBM’s ability to simplify IT service management with cloud freed AXA to accelerate its digital transformation, drive innovation, and reimagine their customer value proposition. For AXA Hong Kong and Macau (AXA), the market landscape was changing fast. A strong international customer base built by offering protection, wealth management, and retirement solutions was no longer […]



