Cybersecurity
What Can Games Teach Us About Cybersecurity?
May 22, 2020 | Written by: John Clarke
Categorized: Cybersecurity
Share this post:

Hayley Cohen, an IBM gamification engineer, leads a cyber attack simulation at the IBM Security Command Center in Cambridge, Mass.
Cybersecurity is essential. But building a strong security culture is a struggle for many organizations. New processes and structures need to be created and adopted for securing users, data and applications—wherever they are, including in the cloud. That means managing change, training and persuading teams to do things differently than they have before. Increasingly, training programs use game techniques to make learning interesting and motivating.
Gamification, as it’s called, involves applying game design elements and principles in non-game contexts. As an example, shoppers may and use them when buying groceries. The more points you get through purchases, the bigger the discount or number of coupons for your next trip to the grocery store or online shopping spree. There are also other elements, like competition with others, rules of engagement, timers and badges, to motivate players and reward behaviors. Games also usually have an end goal or win state.
What happens when you take those elements and apply them to cybersecurity? My team at IBM devises simulated cyberattack scenarios that use gamification to create immersive simulations in the IBM Security Command Centers. These are designed to help diverse teams learn how to work together to prepare for a real-world cyberattack. C-suite, department managers and IT and security staff go through a series of realistic intrusions, learning to use security tools and design thinking to prepare them for their worst day: a cyber breach that can cost millions of dollars to recover from, harm customers and damage reputation.
IBM’s three Command Centers—one in Cambridge, Mass., one in Atlanta and a mobile version based inside a truck that serves clients across Europe—have hosted training sessions for more than 5,000 client participants from a wide range of industries, including some of the biggest banks and government organizations. Some of these organizations have experienced incident response teams, adept at practicing their response plans and honing their skills. For them, stress-testing their playbooks for specific events like a ransomware attack or an insider threat is critical to their ability to respond to such an event in the real world. All of this they can do within the confines of the Command Center, allowing them to make the mistakes and changes necessary to fine-tune their response.
Other organizations, however, are just beginning the process of building the muscle memory required for individuals and teams to fluidly respond to rapidly changing and unpredictable circumstances. The use of simulated and gamified immersive scenarios can bring teams to a point where the response to a breach becomes second nature. Beginning this process early will allow a team to mature a lot faster for the dreaded day of a cyber incident.
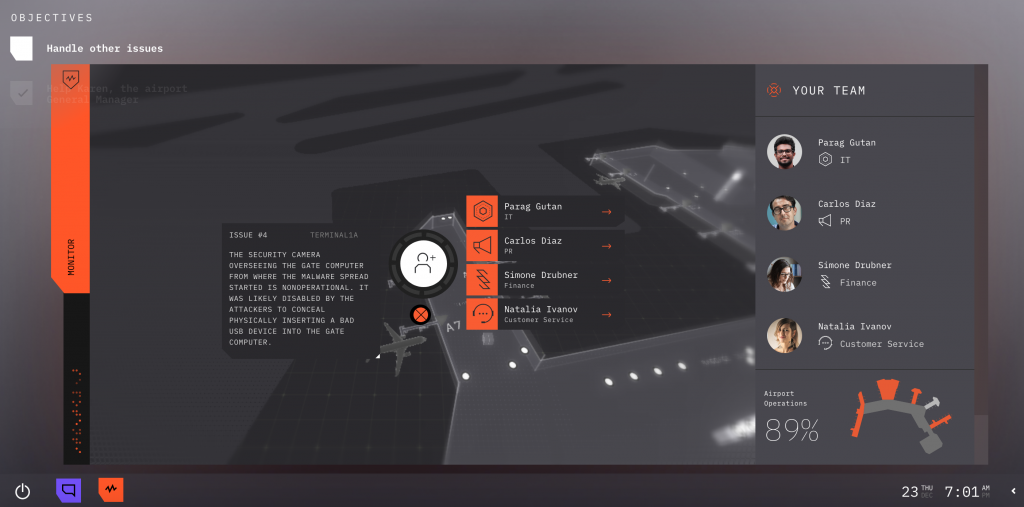
The IBM-designed video game “Cybersecurity Ops: Terminal” simulates an airport cyberattack.
With these simulation games, it’s important to apply pressure to cognitive and emotional responses in ways that tabletop exercises can’t match. When time is ticking, phones are ringing with questions from media and government officials, reports are coming in that systems are offline and the company stock starts tanking, participants recognize and understand how an unplanned and uncoordinated response can lead to costly mistakes. This helps teams learn those responses and reduce response times so they are better prepared in a real situation.
By borrowing from real breaches out of the headlines, and an array of attack types in a chain of events mimicking the techniques of cyberattackers, gamified attack scenarios in our Command Centers can reveal gaps in a team’s incident response playbook.
A simulated breach is not too different from a fire drill. And like a fire drill, the experience helps people react in a real situation almost without thinking. Where are the fire extinguishers? Where are the exits? What decisions have to be made to make sure everyone is safe, put out the fire and assess the damage?
In a cyber situation, you must quickly figure out what’s happening and know what to do next. You have to consider health and safety, manage information and communication, and handle a flood of issues from data analysis to legal requirements. A full business response is required from many different teams. Practicing in a game-like environment helps make those connections.
As our Command Center teams run more of these scenarios, we see the ways our customers react, how they falter and how they succeed, and we can apply these findings to create better challenges. They practice, we practice. They learn, we learn.
All these concepts are rolled into the latest gamification project created by the Command Center team and our design and developer partners. “Cybersecurity Ops: Terminal” is a video game that aims to bring a facsimile of the Command Center experience to a broad audience, and to raise awareness of cybersecurity threats and what it takes to fight them.
Just like the Command Center challenges, the goal of “Terminal” is to immerse you in the scenario and ramp up the pressure as the attack unfolds. Playing different roles, the decisions you make can come back to haunt you down the line. Do you take that call from the reporter? What should you tell her is happening? Critical systems are compromised. Do you shut down? Remove from the network? What if it is critical to health and safety? Choose carefully and in the right amount of time. The clock is ticking.
In “Terminal,” your decisions and responses are tracked, giving you an overall performance graph at the end to show you how you performed across metrics such as technical response, PR and caring for customers. This is a much simpler form of an attack simulation than what we offer in the Command Centers, and “Terminal” is not intended to act as training for a real event. But the lessons are loud and clear, and it’s also exciting and fun, in my biased opinion.
Simulated, gamified scenarios teach by doing. Or should I say, teach by playing? You can try the “Terminal” game at ibm.com/terminal to get just a taste of what it might feel like on the hotseat of responding to a real cyberattack.

John Clarke is a cybersecurity and gamification strategist at IBM.
Making the workplace safe for employees living with HIV
The recent promising news about Covid-19 vaccines is in sharp contrast to the absence of a vaccine for HIV, despite decades of research. Unlike Covid-19 with a single viral isolate that shows minimal diversity, HIV circulates in a wide range of strains that so far have proven impervious to a single vaccine. Fortunately, more people […]
Call for Code for Racial Justice Needs You: Join the Movement
IBM has never avoided taking on big challenges. At IBM, we are privileged to drive impact at scale. We take on challenges that transform our clients, impact people’s lives and innovate for future generations as we strive to effect systematic societal change. Over the course of our 109-year history, the evidence has become clear that […]
A New Wave: Transforming Our Understanding of Ocean Health
Humans have been plying the seas throughout history. But it wasn’t until the late 19th century that we began to truly study the ocean itself. An expedition in 1872 to 1876, by the Challenger, a converted Royal Navy gunship, traveled nearly 70,000 nautical miles and catalogued over 4,000 previously unknown species, building the foundations for modern […]


